Server intrusion handling process
2023-11-15 05:45:42
Today, the developer said that the server was slow, so let's see what's going on. Then there is the following content.
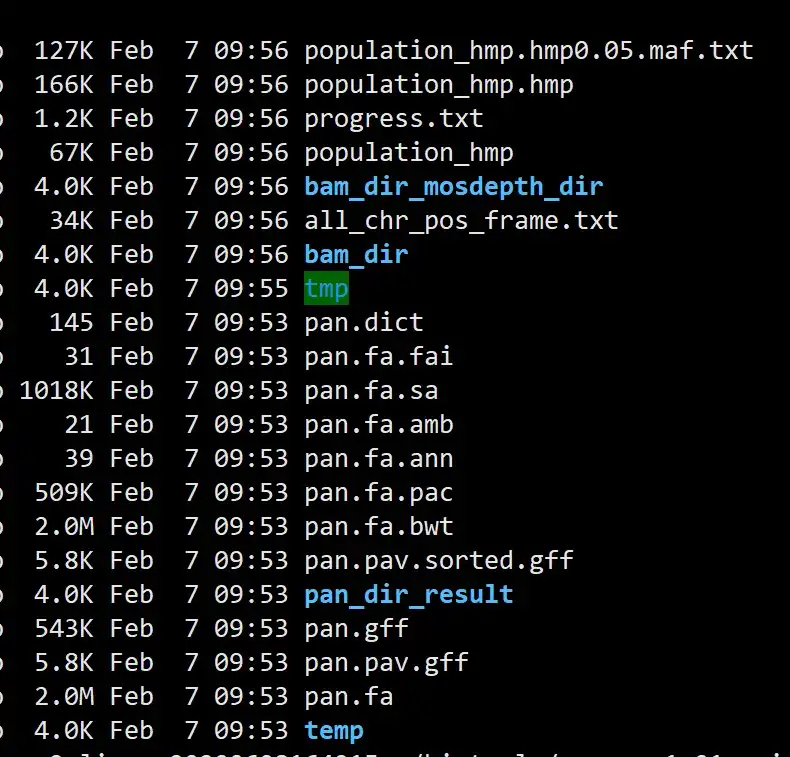
At first glance, kswapd0 is a kernel process, but if you look closely, you will find that the USER is novel, which is abnormal. It should be root normally.
The subsequent hardening can set ssh to not allow login with passwords, but to use more secure keys to log in.
[root@server ~]# ps aux | grep -v grep | grep novel
User PI %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
novel 1233 0.0 2.2 601400 16264 pts/0 S+ 09:42 0:00 /bin/bash
novel 1234 0.0 2.3 601400 17704 pts/0 R+ 09:42 0:00 ps aux
novel 1235 1.3 7.8 1375008 669496 pts/0 R+ 09:42 0:00 sftp-server
novel 1236 2.2 8.8 1720500 746824 pts/0 R+ 09:42 0:00 sftp-server
novel 1237 2.3 8.9 1720500 749008 pts/0 R+ 09:42 0:00 sftp-server
novel 1238 0.0 0.6 63780 5080 pts/0 S+ 09:42 0:00 /bin/sh /opt/lampp/lampp start
novel 1239 0.0 0.6 63780 5008 pts/0 S+ 09:42 0:00 /bin/sh /opt/lampp/lampp start
novel 1240 0.0 0.6 63780 5012 pts/0 S+ 09:42 0:00 /bin/sh /opt/lampp/lampp start
novel 1241 0.0 0.6 63780 5048 pts/0 S+ 09:42 0:00 /bin/sh /opt/lampp/lampp start
[root@server ~]# id novel
uid=1000(novel) gid=1000(novel) groups=1000(novel)
[root@server ~]# netstat -an | grep 22 | grep novel
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN
tcp6 0 0 :::22 :::* LISTEN
[root@server ~]# cat /var/log/secure | grep novel
May 29 18:09:34 server sshd[1221]: pam_unix(sshd:session): session opened for user novel by (uid=0)
May 29 18:09:34 server sshd[1221]: pam_unix(sshd:session): session closed for user novel
May 29 18:10:32 server sshd[1223]: Failed password for invalid user novel from 10.1.1.16 port 53697 ssh2
May 29 18:10:33 server sshd[1223]: Failed password for invalid user novel from 10.1.1.16 port 53698 ssh2
May 29 18:10:34 server sshd[1223]: Failed password for invalid user novel from 10.1.1.16 port 53699 ssh2
May 29 18:10:35 server sshd[1223]: Failed password for invalid user novel from 10.1.1.16 port 53700 ssh2
[root@server ~]#
Conclusions:
- The server was invaded due to password login.
- The user novel cracked the password and logged in to the server.
- The user novel executed some commands on the server, such as creating a new user, modifying files, and installing software.
- The user novel used the server to attack other servers.
Handling process:
- Change the login mode of the server and set it to only allow login with keys.
- Modify the password of the root user and other users.
- Check the server logs and find out the abnormal login records.
- Find out the files that the user novel modified and restore them.
- Uninstall the software installed by the user novel.
- Scan the server for viruses and other malware.
- Strengthen the security of the server and install a firewall.
Prevention:
- Set the server login mode to only allow login with keys.
- Set a strong password for the root user and other users.
- Regularly check the server logs and find out the abnormal login records.
- Regularly scan the server for viruses and other malware.
- Install a firewall to protect the server from attacks.